Two-factor authentication (2FA) is an effective way to spice up the safety of your accounts. However even with that added layer of safety, malicious actors are discovering methods to interrupt in. So-called adversary-in-the-middle assaults benefit from weaker authentication strategies to entry accounts. Your two-factor and multi-factor authentication (MFA) could also be weak, however, fortunately, there’s one thing you are able to do about it.
How multi-factor authentication works
MFA makes use of two or extra checkpoints to verify a consumer’s identification for accessing an account or system. That is safer than counting on only a username and password mixture, particularly given how simple many passwords are to crack, and what number of have discovered their method onto the darkish net. Passwords are sometimes primary and repeated, so as soon as a password has been compromised, it may be used to get into many accounts. That is why it is so essential to make use of robust and distinctive passwords for every considered one of your accounts.
With MFA, a password is not sufficient. From right here, the consumer has to validate their login utilizing at the least one extra piece of proof, ideally that solely they’ve entry to. This generally is a data issue (a PIN), a possession issue (a code from an authenticator app), or an identification issue (a fingerprint).
Observe that whereas 2FA and MFA are sometimes used interchangeably, they don’t seem to be essentially the identical factor. 2FA makes use of two elements to confirm a consumer’s login, similar to a password plus a safety query or SMS code. With 2FA, each elements can one thing the consumer is aware of, like their password and a PIN.
MFA requires at the least two elements, and so they should be impartial: a mixture of a data issue like a password, plus a biometric ID or a safe authenticator like a safety key or one-time password. Usually, the extra authentication elements wanted, the higher the account safety. But when all elements will be discovered on the identical gadget, safety is in danger if that gadget is hacked, misplaced, or stolen.
MFA can nonetheless be compromised
Whereas having MFA enabled in your accounts could make you are feeling safe, some MFA strategies will be compromised nearly as simply as your usernames and passwords.
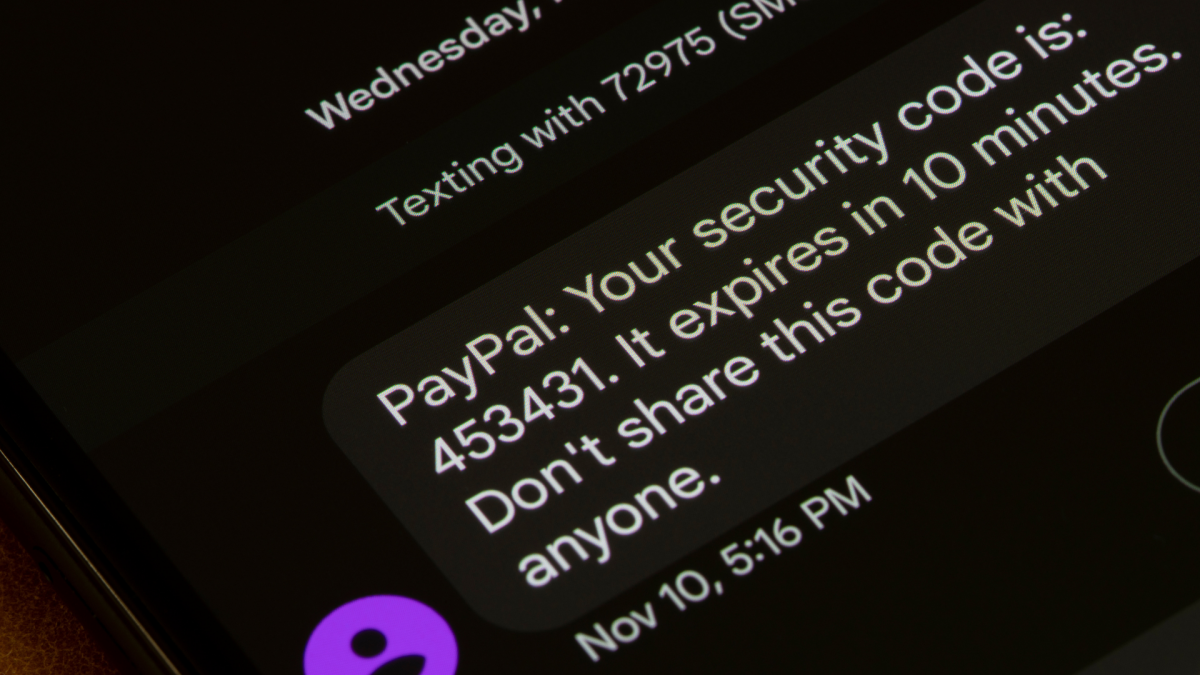
As Ars Technica experiences, sure data and possession elements are themselves prone to phishing. Assaults often called adversary-in-the-middle goal authentication codes, similar to these despatched through SMS and e-mail, in addition to time-based one-time passwords from authenticator apps, permitting hackers to entry your accounts by means of elements you have unknowingly handed them.
What do you suppose up to now?
The assault works as follows: Dangerous actors ship you a message saying that considered one of your accounts—Google, for instance—has been compromised, with a hyperlink to log in and lock it down. The hyperlink appears to be like actual, as does the web page you land on, however it’s really a phishing hyperlink linked to a proxy server. The server forwards the credentials you enter to the actual Google website, which triggers a reliable MFA request (and for those who’ve arrange MFA in your account, there isn’t any purpose to consider that is suspicious). However if you enter the authentication code on the phishing website or approve the push notification, you have inadvertently given the hacker entry to your account.
Adversary-in-the-middle is even simpler to hold out because of phishing-as-a-service toolkits accessible in on-line boards.
How you can maximize MFA safety
To get essentially the most out of MFA, take into account switching from elements like SMS codes and push notifications to an authentication methodology that’s extra proof against phishing. The best choice is MFA primarily based on WebAuthn credentials (biometrics or passkeys) which are saved in your gadget {hardware} or a bodily safety key like Yubikey. Authentication works solely on the actual URL and on or in proximity to the gadget, so adversary-in-the-middle assaults are practically inconceivable.
Along with switching up your MFA methodology, you must also be cautious of the same old phishing pink flags. Like many phishing schemes, MFA assaults prey on the consumer’s feelings or anxiousness about their account being compromised and the sense of urgency to resolve the issue. By no means click on hyperlinks in messages from unknown senders, and do not react to supposed safety points with out checking their legitimacy first.